
Publishing Outlook Web Access (OWA) with Forefront TMG 2010
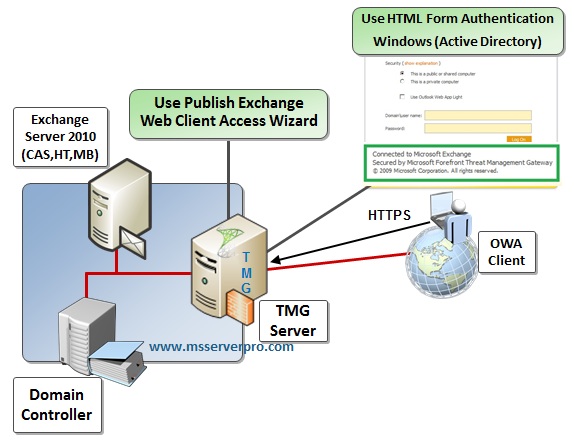
In this article, we take a look into configuration for Publishing Outlook Web Access (OWA) with Forefront TMG 2010. We will use HTML Forms authentication with Windows (Active Directory) Validation. To use Windows (Active Directory) authentication method, TMG 2010 must be a domain member. In Exchange 2010, we have to select Integrated Windows and Basic authentication for OWA. OWA is pre-authenticated at TMG 2010 rather than at Client Access Server. This will make sure that only TMG validated sessions are passed onto the Client Access Server.
In Exchange 2010, the CAS role handles both external and internal connections to the Mailbox role (with the exception of Public Folder connections). Outlook Web App is one of the CAS (Client Access Server) role aspects which allow you to access email through a Web browser (including IE, Firefox, Safari and Google Chrome). CAS (Client Access Server) must be deployed in each Active Directory site. TMG placed before CAS then filters unwanted traffic from external connections, that is to say, no unauthenticated traffic reaches the Intranet servers.
Perform the following steps to configure Outlook Web Access (OWA) with TMG 2010:
Step 1. Export the SSL certificate from the Client Access Server.
Step 2. Import the SSL certificate on TMG 2010 Firewall.
Step 3. Create a Web listener (SSL) for use to OWA.
Step 4. Configuring Publishing rule for Outlook Web Access (OWA)
Step 5. Configuring the Client Access Server to change authentication method.
Step 6. Testing the Outlook Web Access Publishing rule from the Web client.
Step 7. Redirect HTTP requests to HTTPS (Optional)
Step 1. Export the SSL certificate from the Client Access Server
1. On the Exchange 2010 Server (KTM-EX01-2K10), open the Exchange Management Console and navigate to Server Configuration. Right-click the Microsoft Exchange certificate which is not self- signed (MSSERVERPRO Mail Certificate), and then clicks Export Exchange Certificate.
2. On the Introduction page, click Browse, and then browse to drive C, type OWAssl.pfx as the file name, and then click Save. In the Password field, type XXXXXXX, click Export, and click Finish. Then copy the exported certificate file to the local disk (drive C:) of the TMG Server.
Step 2. Import the SSL certificate on TMG 2010 Server.
1. On the Forefront TMG Server (KTM-TMGSRV), click Start, Run and type MMC and then press Enter.
2. On the File menu, click Add/Remove Snap-in.
3. On the Add or Remove Snap-ins page, click Certificates, and then click Add.
4. Click Computer account, click next, click Finish, and then click OK.
5. In the Console1 tree, Expand Certificates node, Expand the Personal folder, Right-click Certificates choose All Tasks, and then click Import.
6. On Welcome to the Certificate Import Wizard page, click Next.
7. On the File to Import page, type the location where the certificate is located. Here our certificate file is located in c:\OWAssl.pfx, and then click Next.
8. On the Password page, type the password for the file. Do not put a checkmark in the checkbox labeled Mark this key as exportable, and then click Next.
9. On the Certificate Store page, Place the certificate in the Personal certificate store and click Next.
10. Review the settings on the Completing the Certificate Import page and then click Finish. Click OK on Complete the wizard and confirm that the import was successful. The imported certificate will now appear in the right pane of the console. The SSL certificate must be placed into the Trusted Root Certification Authorities\Certificates store so that this server will trust the Web site certificate installed on it.
Step 3. Create a Web listener (SSL) for use to OWA
1. In the Forefront TMG Management console, Click Firewall Policy node, on the right side of the console, click the Toolbox tab, Expand Network Objects.
2. Under Network Objects, click New and then click Web Listener.
3. On the Welcome to the New Web Listener Wizard page, type the web listener name in the Name box, OWA SSL and then click Next.
4. On the Client Connection Security page, select Require SSL secured connections with clients, and then click Next.
5. On the Web Listener IP Addresses page, select External network as TMG will be listening to requests from clients on the External adapter.
6. On the Listener SSL Certificates page, click the Select Certificate button to display the list of available certificates and select the certificate we installed earlier and then click Select and then click Next.
7. On the Authentication Settings page, select HTML Form Authentication in the drop-down box from the Select how clients will provide credentials to Forefront TMG, and then select Windows (Active Directory) as the service that will authenticate collected credentials and then click Next.
Note: To use Windows (Active Directory) authentication method, Forefront TMG 2010 must be a domain member.
8. On the Single Sign On Settings page, select Enable SSO for Web sites published with this Web listener, and type, .msserverpro.com as the single sign-on domain and then click Next.
9. On the Completing the New Web Listener Wizard page, review the configuration and then click Finish to create the Web listener.
10. Click Apply twice to save changes and update the configuration and click OK to saving Configuration Changes.
Step 4. Configuring Publishing rule for Outlook Web Access (OWA)
1. In the Forefront TMG Management console, click the Firewall Policy node. In the right pane, click the Tasks tab. In the Task pane, click Publish Exchange Web Client Access.
2. On the Welcome to the New Exchange Publishing Rule Wizard, type Publishing Outlook Web Access as the name of the rule and then click Next.
3. On the Select Services page, select Exchange Server 2010 as the version of Exchange Server to publish and then select Outlook Web Access and then click Next.
4. On the Publishing Type page, select Publish a single Web site or load balancer and then click Next.
5. On the Server Connection Security page, select Use SSL to connect to the published Web server or server farm and then click Next.
6. On the Internal Publishing Details page, type mail.msserverpro.com in the Internal site name, and then click Use a computer name or IP address to connect to the publish server, type the IP Address of the Client Access Server in the Computer name or IP Address. Click Next.
7. On the Public Name Details page, accept the default to only accept requests for This domain name (type below), and type mail.msserverpro.com and then click Next.
8. On Select Web Listener page, select OWA SSL from the Web listener drop-down list and then click Next.
9. On the Authentication Delegation page, select Basic authentication and then click Next.
10. On the User Sets page, accept the default and then click Next.
11. On the Completing the New Exchange Publishing Rule Wizard page, review the rules and then click Finish.
12. Click Apply twice To save changes and update the configuration and then click OK Saving Configuration Changes.
Step 5. Configuring the Client Access Server to change authentication method.
1. In the Exchange Management Console tree, expand Server Configuration, click Client Access Node, click Outlook Web App and then double-click owa (Default Web Site)
2. On the OWA(Default Web Site) Properties dialog box, click on the Authentication tab, click Use one or more standard authentication methods, select the Integrated Windows authentication and the Basic Authentication (password is sent in clear text check box) and click Apply and then click OK twice.
3. In the Exchange Management Shell, at the PS Prompt, type iisreset /noforce and then press Enter.
Step 6. Testing the Outlook Web Access Publishing rule from the Web client.
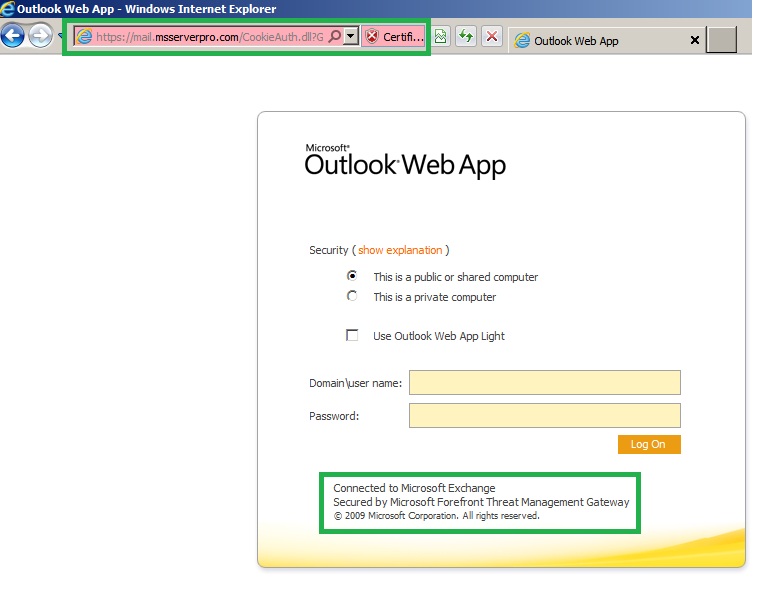
1. Log on to the Web client, open Internet Explorer, and browse https://mail.msserverpro.com/owa
Note: Here we are using Private Internal CA Server. Therefore public computer does not auto-trust our Internal CA Certificate.
Note: Microsoft recommend always used public certificate for OWA. If you we use Public CA Certificate, our web browser auto-trust the CA Certificate. For example,
Steps 7. Redirect HTTP requests to HTTPS
This setting automatically redirects HTTP traffic to HTTPS. So this will help users access their OWA without typing https at the beginning (http://mail.msserverpro.com/owa). It will automatically redirect to https://mail.msserverpro.com/owa. This helps end users access their web mail, Outlook Web Access (OWA) without any hassle over https protocol.
Summary:
Exchange Server, Client Access Server (CAS) directly facing the Internet without Forefront TMG 2010 is susceptible to attacks and TMG adds a layer of authentication and added security. Forefront TMG 2010 allows pre-authentication before the traffic is forwarded to the Client Access Server (CAS). That way, Exchange Deployment is protected with additional Layer of Security as illustrated in the screenshots above.






















































Good Job.
Pingback: Publishing Outlook Web Access (OWA) with Forefront TMG 2010 | Popular Stuff You Need To Know
hy,
In this tutorial you not used public cert is it possible to publish internal cert.well, what is the use by redirecting http to https using isa/tmg by default exchange OWA using https protocol and if i want to publish owa in standalone ISA/TMG is it possible.
This is my lab environment so I am using Internel CA. We can use Internal CA as well but users get Warning message “There is a probem with this websit’s security certificate” , every time they log on in OWA from the Public network. Therefore, I recommend always used public CA for OWA because OWA is mainly access from the public network.